Office365 Data Breach Nets Millions For Crook, Federal Investigation Reveals
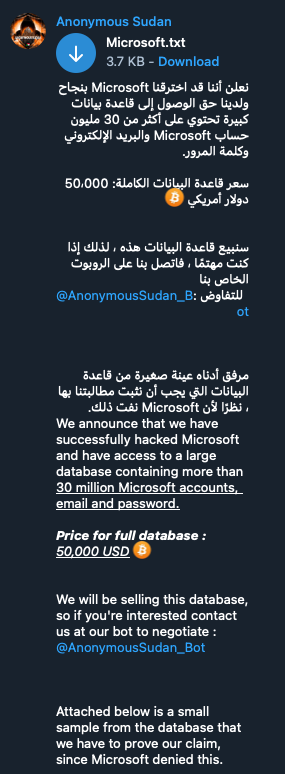
Table of Contents
The Scale of the Office365 Data Breach
The investigation revealed a staggering impact from this Office365 data breach. The theft of millions of dollars from multiple businesses represents a significant financial loss, impacting everything from small startups to established corporations. Thousands of Office365 accounts were compromised, potentially exposing sensitive customer data including personal information, financial records, and intellectual property. This Office365 data loss extends far beyond simple monetary theft; it encompasses reputational damage and potential legal liabilities for affected companies.
- The financial impact: The exact amount stolen is still under investigation, but early estimates place the losses in the millions of dollars. The diversity of affected businesses suggests the attacker targeted a wide range of vulnerabilities, highlighting the broad reach of this Office365 security flaw.
- Compromised accounts: The sheer number of compromised accounts points to a sophisticated attack that exploited a weakness allowing for mass compromise. The potential for further data breaches and exploitation remains a concern.
- Exploited vulnerability: The investigation is still working to pinpoint the specific vulnerability, but early indications suggest a previously unknown flaw in the Office365 platform. This underscores the constant need for vigilance and proactive security measures.
- Methods used: The precise methods used by the cybercriminal remain under investigation. However, it is likely a combination of sophisticated techniques, exploiting known and unknown vulnerabilities to gain access and maintain persistence within the Office365 environment. The long-term consequences for businesses include significant legal battles, regulatory fines, and reputational damage, making proactive Office365 security paramount.
The Federal Investigation: Unraveling the Cybercrime
The FBI is leading the federal investigation into this major Office365 data breach, collaborating with international agencies to track down the perpetrators and unravel the scope of the crime. This complex cybercrime investigation faces significant challenges, as the criminals likely operate across international borders, employing advanced techniques to cover their tracks.
- International collaboration: The global nature of cybercrime necessitates collaboration between multiple law enforcement agencies worldwide. Sharing intelligence and coordinating efforts are crucial for successful prosecution.
- Tracing the funds: Investigators are meticulously tracing the flow of stolen funds through various financial institutions and cryptocurrency exchanges, a complex process that often takes considerable time and resources.
- Identifying accomplices: The investigation is focused on identifying any accomplices or organizations involved in facilitating the breach or laundering the stolen funds. This requires careful analysis of digital evidence and financial transactions.
- Potential charges: Potential criminal charges against those responsible could include wire fraud, identity theft, computer fraud, and conspiracy, carrying significant penalties.
Vulnerabilities Exposed: Office365 Security Gaps
The Office365 data breach exposed several critical security vulnerabilities, highlighting the need for robust security practices within organizations. While the specifics are still emerging from the investigation, several factors likely contributed to the success of this attack.
- Multi-factor authentication weaknesses: Inadequate implementation or lack of enforcement of multi-factor authentication (MFA) likely played a crucial role in allowing attackers to bypass initial security measures.
- Phishing attacks: Phishing attacks, designed to trick users into revealing their credentials, may have been instrumental in gaining initial access to accounts.
- Weak password policies: Lack of strong password policies and the use of easily guessable passwords contributed to the vulnerability of many accounts.
- Inadequate employee training: Insufficient cybersecurity awareness training for employees might have led to vulnerabilities being exploited through social engineering techniques.
Protecting Your Business from Office365 Data Breaches
Protecting your business from Office365 data breaches requires a multi-layered approach encompassing robust security measures and employee training. This Office365 security strategy should proactively address vulnerabilities and minimize risks.
- Strong password policies: Enforce strong password policies, including length requirements, complexity rules, and regular password changes. Encourage the use of password managers.
- Multi-factor authentication: Enable and rigorously enforce multi-factor authentication (MFA) for all Office365 accounts. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Software updates: Regularly update all software and security patches to address known vulnerabilities and close security gaps.
- Employee training: Invest in comprehensive cybersecurity awareness training for all employees, focusing on phishing prevention, password security, and recognizing suspicious activity.
- Cybersecurity solutions: Consider investing in advanced cybersecurity solutions, including intrusion detection systems, security information and event management (SIEM) systems, and endpoint detection and response (EDR) tools.
Conclusion
The Office365 data breach serves as a stark reminder of the ever-present threat of cybercrime. The millions of dollars lost and the sensitive data compromised underscore the critical need for robust Office365 security measures. By implementing strong password policies, utilizing multi-factor authentication, regularly updating software, and educating employees, businesses can significantly reduce their risk of falling victim to similar Office365 data breaches. Don't wait until it's too late – proactively secure your Office365 environment today. Learn more about bolstering your Office365 security and protecting your valuable data.

Featured Posts
-
 Fsu Security Breach Swift Police Response Fails To Quell Student Fears
Apr 22, 2025
Fsu Security Breach Swift Police Response Fails To Quell Student Fears
Apr 22, 2025 -
 Ukraine Conflict Trumps Peace Plan And Kyivs Crucial Decision
Apr 22, 2025
Ukraine Conflict Trumps Peace Plan And Kyivs Crucial Decision
Apr 22, 2025 -
 Los Angeles Wildfires The Rise Of Disaster Betting
Apr 22, 2025
Los Angeles Wildfires The Rise Of Disaster Betting
Apr 22, 2025 -
 Execs Office365 Accounts Breached Millions Made Feds Say
Apr 22, 2025
Execs Office365 Accounts Breached Millions Made Feds Say
Apr 22, 2025 -
 Pope Franciss Legacy The Conclaves Crucial Test
Apr 22, 2025
Pope Franciss Legacy The Conclaves Crucial Test
Apr 22, 2025
